Cloud computing has revolutionized the digital landscape, transforming how businesses operate and secure their data in 2024.
Organizations worldwide are navigating through complex cloud ecosystems while facing unprecedented cybersecurity challenges that demand robust protection strategies.
This comprehensive guide explores the latest cloud computing trends, backed by statistical insights, and outlines practical security measures to help businesses fortify their cloud infrastructure against evolving threats.
The Growth of Cloud Computing: Key Statistics
| Category | Metric | Details |
| Market Size | $1 trillion | Projected market value by 2030 |
| Annual Growth Rate | 15% | Driven by remote work solutions and IT infrastructure demands |
| Major Growth Drivers | • Remote Work Solutions • Scalable Infrastructure • Digital Transformation | Primary factors contributing to market expansion |
| Industry Adoption Rates | Healthcare | • Telemedicine platforms • Patient data storage • Healthcare analytics |
| Retail | • E-commerce platforms • Personalized shopping experiences • Big data analytics | |
| Education | • Remote learning platforms • Digital content delivery • Student data management | |
| Case Study: Netflix | Success Metrics | • Global service scaling • Millions of concurrent users • Seamless streaming capability |
| Edge Computing Integration | IoT Devices | 75 billion devices expected by 2025 |
| Multi-Cloud Adoption | Enterprise Usage | 80% of enterprises using multi-cloud approach |
Current Cloud Trends: What’s Changing?
The cloud computing landscape is undergoing dramatic transformation with the rise of edge computing, multi-cloud deployments, and AI integration reshaping how businesses leverage cloud technologies.
These emerging trends are driving innovation while creating new challenges for security teams to address.
Edge Computing and IoT Integration
Edge computing brings data processing closer to information sources. Smart cities deploy edge computing solutions to manage traffic systems and public utilities.
Manufacturing plants utilize IoT sensors to monitor equipment performance and predict maintenance needs.
The combination of edge computing and IoT devices reduces latency and improves real-time decision-making.
Multi-Cloud and Hybrid Cloud Strategies
Organizations adopt multi-cloud strategies to avoid vendor lock-in and optimize costs. Hybrid cloud solutions combine private and public cloud resources for enhanced flexibility.
Companies maintain sensitive data on private clouds while leveraging public cloud scalability for less critical operations.
AI and Machine Learning Integration
Cloud providers integrate artificial intelligence capabilities into their services. Machine learning algorithms analyze vast datasets to detect security threats and anomalies.
AI-powered automation tools streamline resource allocation and performance optimization. Predictive analytics help organizations make data-driven decisions.
The Evolving Threat Landscape in Cloud Security

In today’s rapidly evolving digital landscape, cloud security threats have become increasingly sophisticated, with cybercriminals employing advanced tactics to breach organizational defenses.
Recent statistics reveal a 300% surge in cloud-based attacks, making robust security measures more critical than ever for business continuity and data protection.
Common Threats
Data breaches expose sensitive information to unauthorized users. Ransomware attacks encrypt cloud-stored data for financial extortion.
Insider threats pose significant risks through privileged access misuse. Configuration errors lead to unintended data exposure.
Recent High-Profile Breaches
A major healthcare provider experienced a breach affecting 10 million patient records.
A financial services company lost $5 million through a cloud-based ransomware attack. A retail giant’s misconfigured cloud storage exposed customer data for 48 hours.
Statistics
Organizations face an average of 2,200 cyber attacks daily. Cloud security breaches cost companies $4.5 million on average. Ninety percent of organizations experienced at least one cloud security incident last year.
READ THIS BLOO: Clayton Grimm Net Worth in 2025
Robust Cloud Security Strategies
Modern cloud security demands a comprehensive approach that combines advanced encryption, identity management, and real-time threat detection to safeguard digital assets effectively.

Organizations are increasingly adopting zero-trust architectures and AI-powered security solutions to protect their cloud infrastructure against emerging threats.
Understanding the Shared Responsibility Model
Cloud providers secure the infrastructure and platform layers. Customers remain responsible for data security and access management. Clear understanding prevents security gaps and ensures comprehensive protection.
Encryption and Data Protection
Organizations implement end-to-end encryption for data in transit and at rest. Advanced encryption algorithms protect sensitive information from unauthorized access. Regular key rotation enhances data security and compliance.
Identity and Access Management (IAM)
Role-based access control limits user permissions based on job functions. Multi-factor authentication adds extra security layers for user verification. Regular access reviews prevent privilege accumulation and reduce risks.
Continuous Monitoring and Incident Response
Security teams monitor cloud environments 24/7 for suspicious activities. Automated alerts notify administrators of potential security incidents. Incident response plans enable quick action during security breaches.
Real-World Application: Building a Secure Cloud Framework
Implementing a secure cloud framework requires a strategic approach that balances accessibility with robust protection measures.
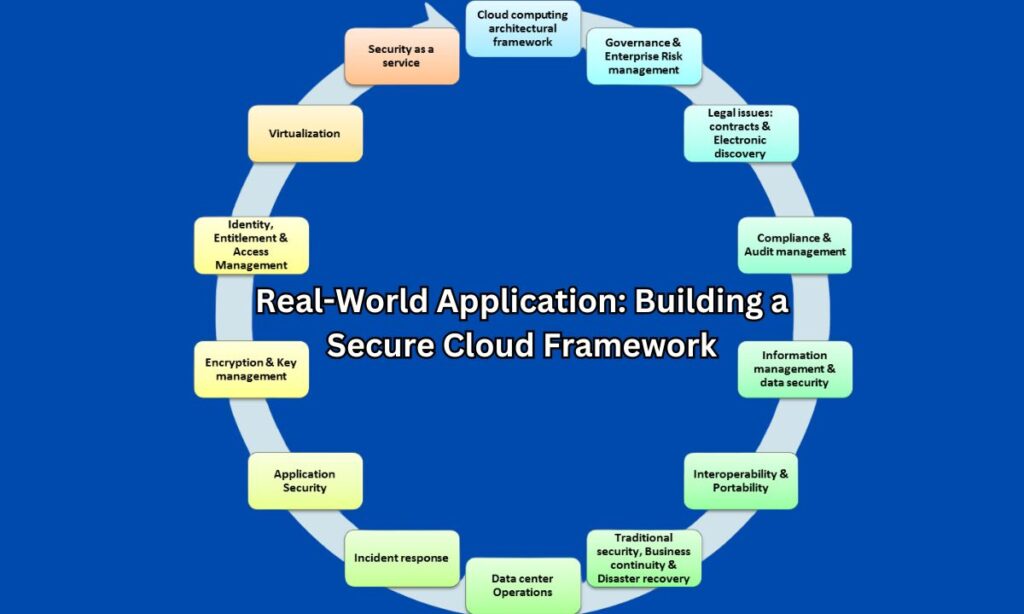
Organizations are now adopting cloud-native security tools and automated compliance monitoring to build resilient infrastructures that can withstand modern cyber threats.
Assess Needs and Risks
Organizations evaluate their specific security requirements and compliance obligations. Risk assessments identify potential vulnerabilities and threats. Security teams prioritize protection measures based on risk levels.
Choose the Right Provider
Companies compare cloud providers based on security features and certifications. Service level agreements define security responsibilities and performance metrics. Provider reputation and track record influence selection decisions.
Implement Security Best Practices
Teams deploy security controls across all cloud environments. Regular security training ensures staff awareness and compliance. Automation tools enforce security policies consistently.
Regularly Audit and Update
Monthly security audits verify control effectiveness and compliance. Teams update security measures based on emerging threats and technologies. Continuous improvement processes enhance overall security posture.
Success Story
A global retailer implemented comprehensive cloud security measures. Their security incidents decreased by 75% within six months. Customer trust improved, leading to increased online sales.
The Human Element in Cloud Security
Despite technological advancements, human factors remain crucial in maintaining cloud security, with 95% of security breaches involving human error.
Organizations must focus on comprehensive training programs and security awareness initiatives to create a culture where every employee becomes an active participant in maintaining cloud security.
Training and Awareness
Regular security training sessions keep employees informed about best practices. Phishing simulations test and improve security awareness. Team members understand their role in maintaining cloud security.
Building a Security-First Culture
Leadership promotes security awareness across the organization. Security considerations integrate into all business decisions. Teams celebrate security successes and learn from incidents.
Examples of Human Error
An employee accidentally shared sensitive data through misconfigured permissions. A developer pushed encryption keys to a public repository. An administrator delayed critical security updates.
Frequently Asked Questions
What is the shared responsibility model in cloud security?
Cloud providers secure infrastructure while customers protect their data and manage access.
Why is multi-factor authentication important?
It adds extra security layers beyond passwords, significantly reducing unauthorized access risks.
How often should security audits occur?
Monthly audits ensure regular assessment of security controls and compliance requirements.
What role does AI play in cloud security?
AI detects threats, automates responses, and enhances security monitoring capabilities.
How can organizations build a security-first culture?
Through regular training, leadership support, and integrating security into business processes.
Conclusion
Cloud computing continues transforming business operations while presenting evolving security challenges. Organizations must implement comprehensive security strategies combining technology, processes, and people. Success requires continuous adaptation to emerging threats and technological advances.

David is a seasoned SEO expert with a passion for content writing, keyword research, and web development. He combines technical expertise with creative strategies to deliver exceptional digital solutions.